Overview
This project is a simulated case study inspired by real-world work I delivered in a client engagement. All proprietary assets have been omitted to preserve client confidentiality, but the architecture and engineering reflect actual problem-solving and implementation strategies.
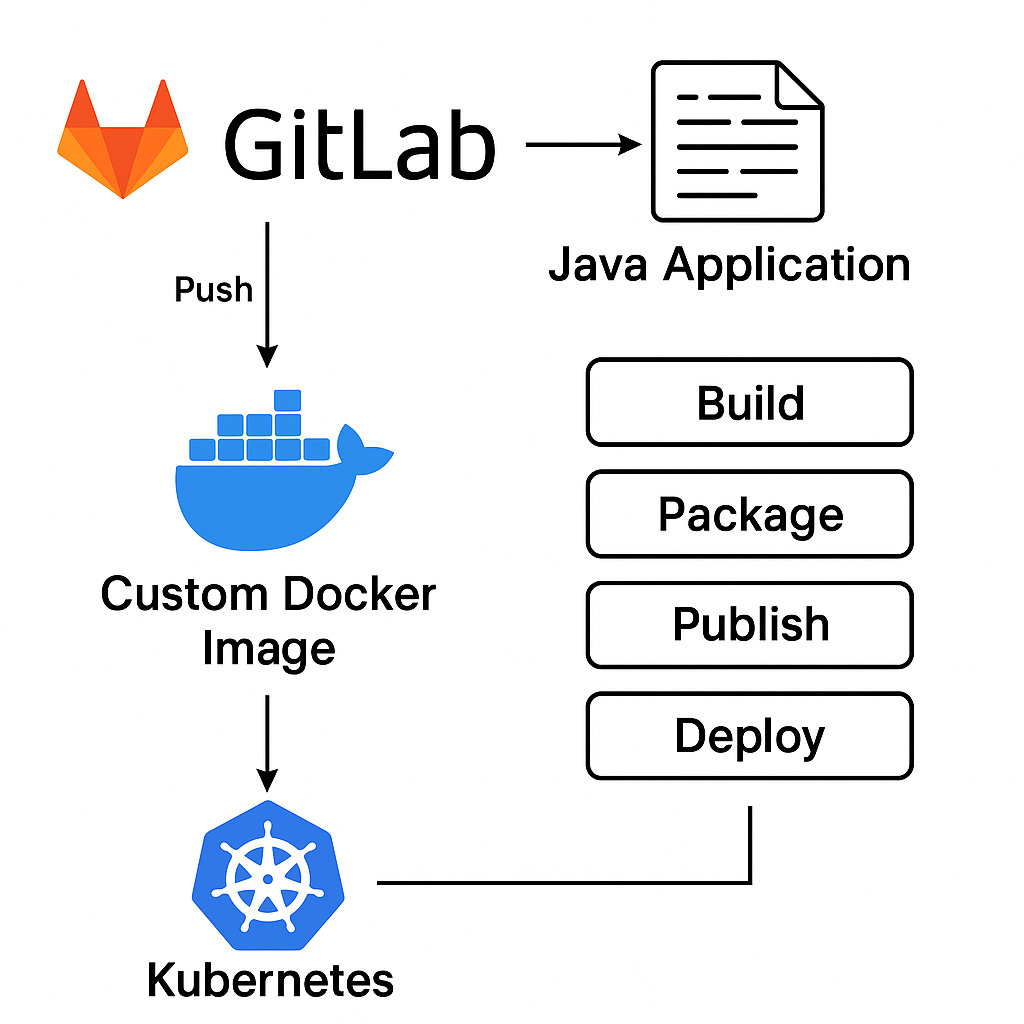
The project demonstrates a production-grade GitLab CI/CD pipeline designed to automate the build, containerization, and deployment of Java-based applications into a Kubernetes environment. The pipeline uses a custom Docker image preloaded with key DevOps tools to ensure fast, consistent, and isolated builds.
Pipeline Architecture
Screenshots
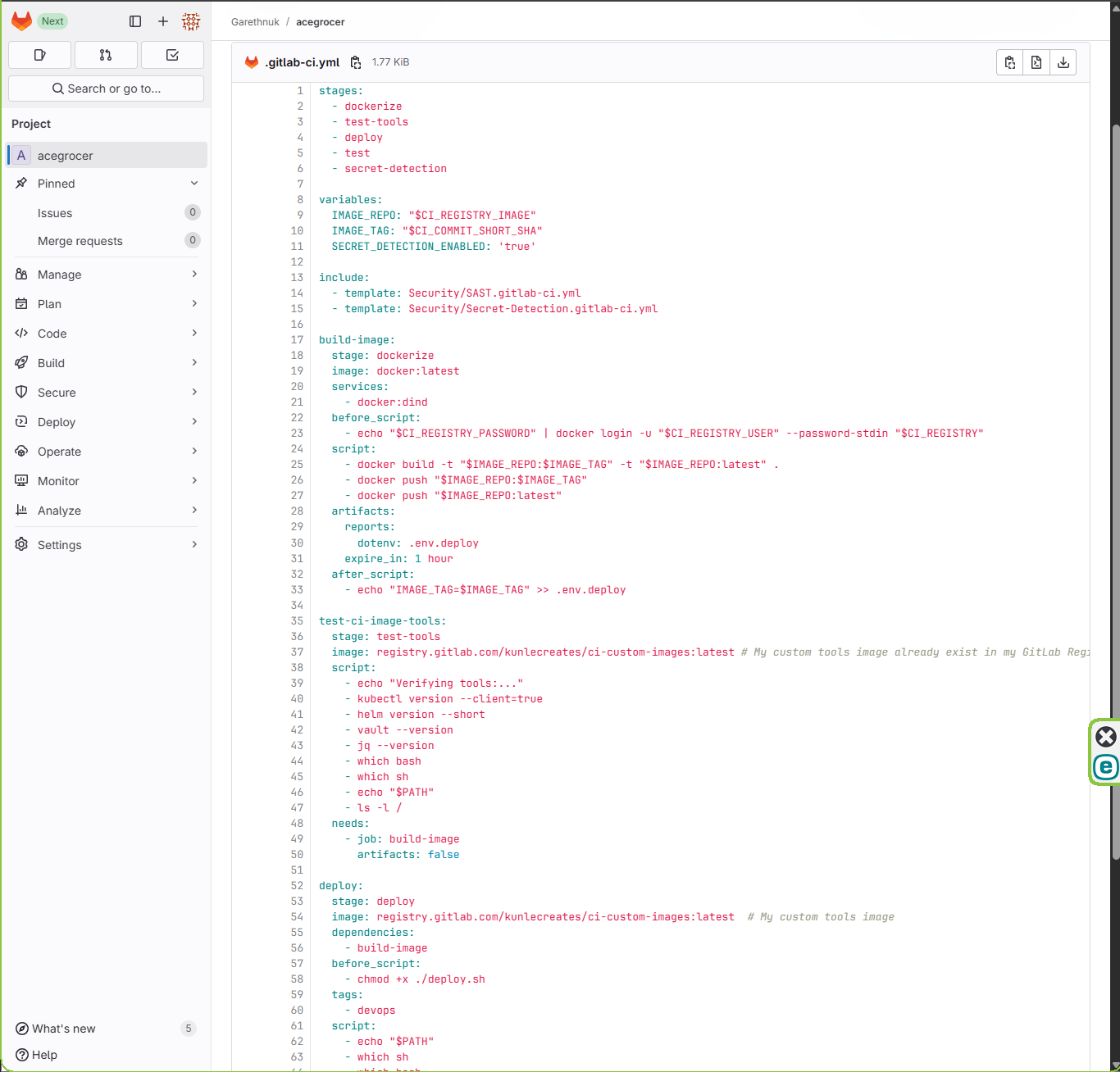
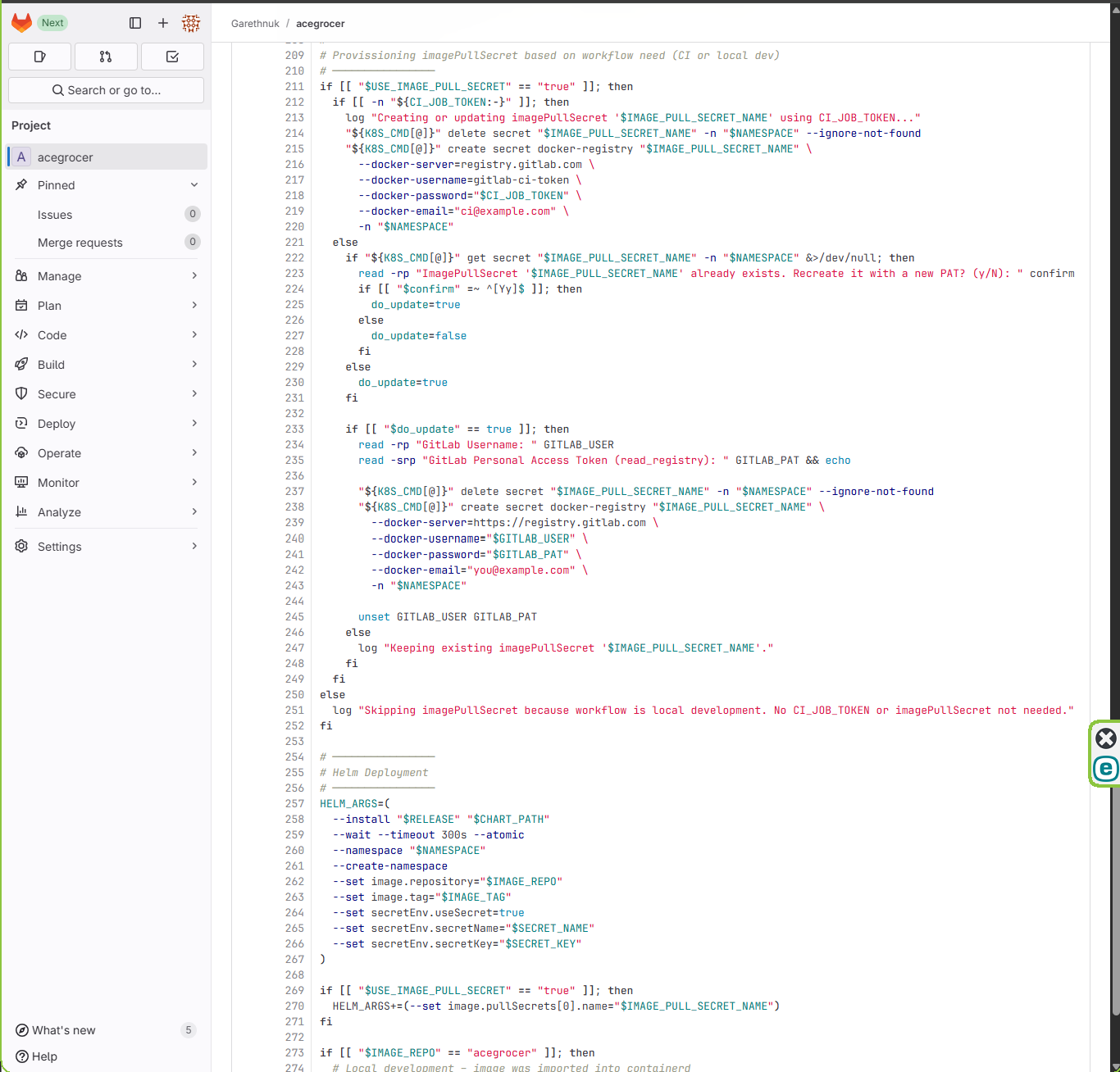
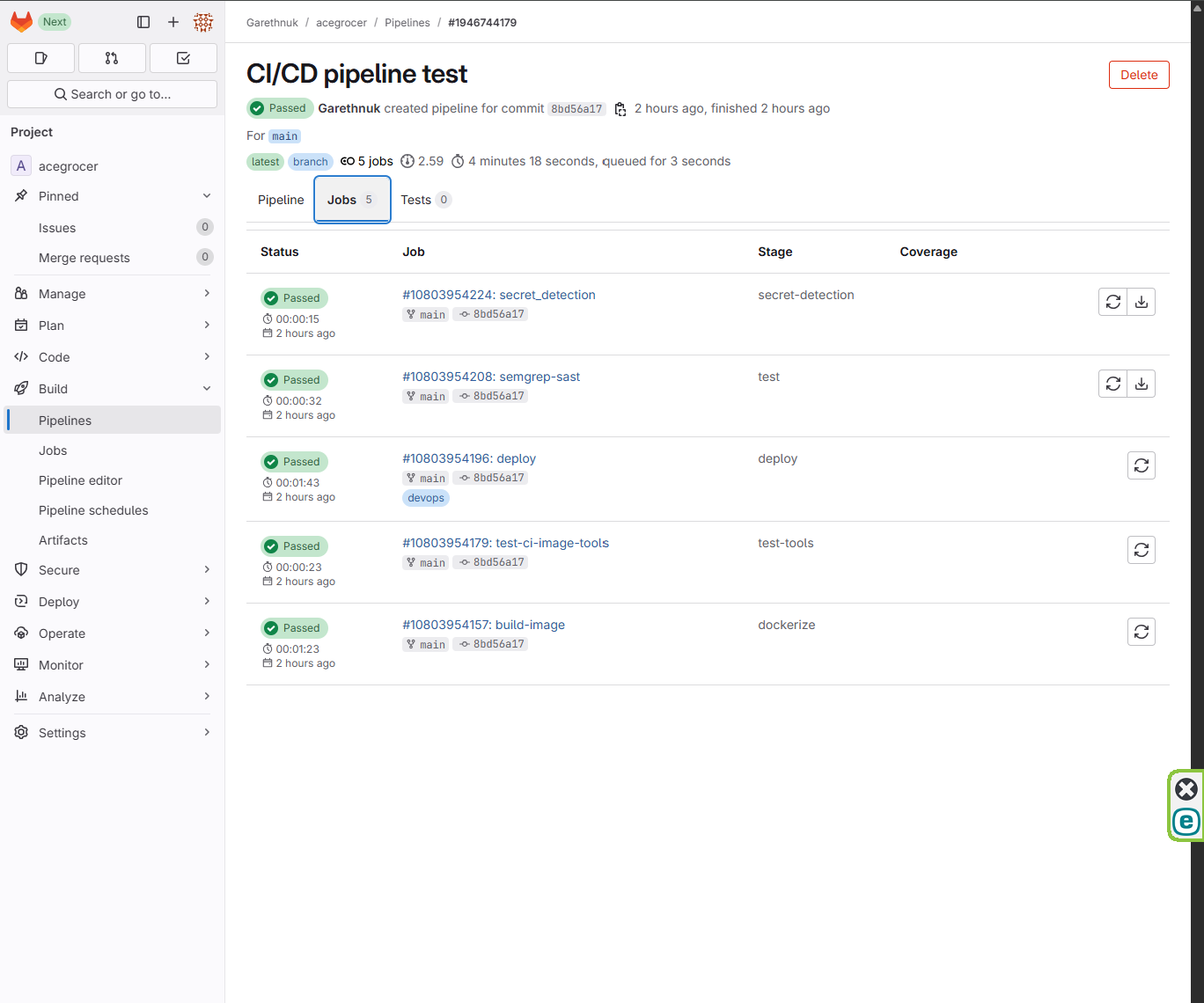
UI Walkthrough (GIF Preview)
Workflow Description
- Code is pushed to a private GitLab repository triggering the pipeline.
- A custom GitLab Runner uses a prebuilt Docker image containing:
kubectl- For cluster interactionHelm- For templated deploymentsbashand core Linux CLI tools - For scripting automation
- The pipeline stages are organized into:
- Build - Maven builds the Java Spring Boot service
- Package - Docker builds and tags the image
- Publish - Image is pushed to GitLab's container registry
- Deploy - Bash scripts and Helm charts apply updates to Kubernetes. A GitLab Project Runner deployed in the k8s cluster executes this stage
- Test - Static Application Security Testing (SAST) is used to discover vulnerabilities in the source code, or identify security issues during development when they’re easiest and most cost-effective to fix
- Secret Detection - Secret Detection customization to scan deployed containers for sensitive credential leaks
- Helm values are templated per environment (dev/staging/prod).
- Each deployment includes instrumentation hooks for observability.
Features Implemented
- Private container registry integration using GitLab's built-in registry
- Custom Docker image with pre-installed tools to speed up execution
- Pipeline YAML includes linting, image tagging, and Helm chart validation
- Declarative deployment through version-controlled Helm charts
- Environment variables and secrets injected securely through GitLab CI/CD settings
Custom Docker Image
The GitLab Runner executes jobs inside a custom Docker image hosted in a private registry. The image includes:
- Helm
- kubectl
- Maven
- Git, Bash, and essential tools
This reduces setup time during builds and ensures consistent behavior across stages.
Example Snippets
.gitlab-ci.yml
image: registry.gitlab.com/kunle/tools:ci-helm-kubectl
stages:
- build
- deploy
build-app:
stage: build
script:
- mvn clean package
- docker build -t $CI_REGISTRY_IMAGE:$CI_COMMIT_SHORT_SHA .
- docker push $CI_REGISTRY_IMAGE:$CI_COMMIT_SHORT_SHA
deploy-to-k8s:
stage: deploy
script:
- helm upgrade --install app ./helm-chart --namespace dev --set image.tag=$CI_COMMIT_SHORT_SHA
Use Cases
- Fully automated delivery pipeline for containerized Spring Boot apps
- Repeatable Helm-based deployments across namespaces/environments
- Fast iterative testing for local-to-cluster development flow
Challenges Solved
- Time lost to manual deployments and inconsistent dev environments
- Need for isolated, reproducible CI/CD runners across projects
- Environment drift between staging and production clusters
Demo or Walkthrough
This project is hosted in a private GitLab repo. Interested reviewers can contact me for a walkthrough of the CI/CD pipeline YAML, runner image Dockerfile, and Helm chart structure.
Request access by reaching out via email.